Trusted by leaders and disruptors



%201.png)






%201.png)






%201.png)



the right detection model for the right moment
In-Stream Detection
Regain control over where data lands, how it's shaped, and what it costs—before a single byte hits storage or analytics.
Historical Detection
Low-and-slow analysis, retroactive detection, investigations, and hypothesis testing against stored data. Find what others missed.
DECOUPLED Detection
Execute analytics where data already lives—without forcing wholesale ingestion. Detection logic goes to the data, not the other way around.
unbounded
Detection is no longer bound to storage. It is a capability that can be composed, scaled, and evolved independently.
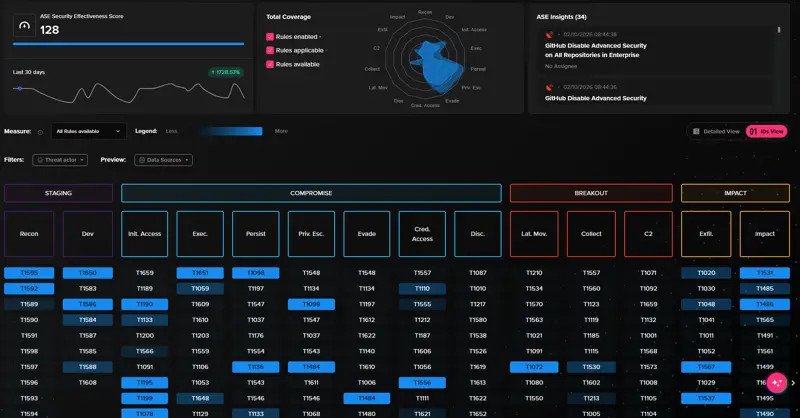
The shift is subtle but important. Modern security operations rely on multiple detection models, each optimized for a different purpose and time horizon. In a composable SIEM, detection logic is portable—it can be pushed into the data stream, executed against historical stores, or federated across external systems.
.png)
portable detection logic
Push detection into the data stream, execute against historical stores, or federate across external systems—without rewriting rules.
Decoupled from Storage
Detection doesn't require that all data be centralized, indexed, or treated equally. It needs reliable, consistent data—wherever it lives.
Outcomes Over Ingestion
Prioritize signal quality, detection coverage, and response speed—not the volume of data being collected and indexed.
Independently Scalable
Scale detection independently from collection and retention. Add new engines, new models, new logic—without re-architecting the stack.
ABSTRACTED
We would love you to be a part of the journey, lets grab a coffee, have a chat, and set up a demo!
Your friends at Abstract AKA one of the most fun teams in cyber ;)
.png)
Your submission has been received.










