Trusted by leaders and disruptors



%201.png)







%201.png)






%201.png)



PROBLEMS OF TODAY’S SIEM “ECOSYSTEM”
Vendor lock-in holds teams hostage
Security teams are trapped in someone else's roadmap. Every "upgrade" is either a rip-and-replace or a costly bill for overlapping features.
Stuck in the data “swamp”
All data gets treated the same—indexed, stored, priced identically—whether it's critical threat telemetry or compliance logs you'll never query. Storage costs spiral. You're either broke or blind.
The Economics Are Broken
Modern SIEM pricing scales with data volume. Security data grows 25–30% annually. Cloud-native environments multiply log sources. Compliance forces long retention. Most stored data is rarely queried.
THE Architecture Is Coupled
Legacy SIEMs were built as monoliths where everything is tightly bound.That creates three downstream issues:You can’t upgrade detection without touching storage. You can’t change storage without replatforming. You can’t route data intelligently before it hits the billing meter. Detection becomes constrained by indexing models designed 10–15 years ago.
In a multi-cloud, streaming world, that coupling is a liability.
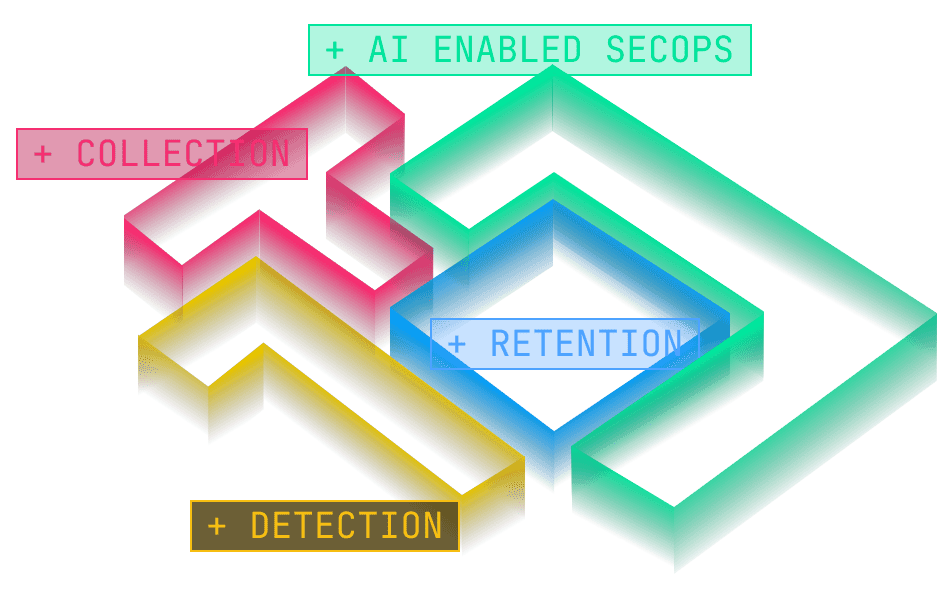
Abstract is Composable SIEM, a flexible, composable platform where each function can be swapped, scaled, or integrated. A platform that evolves at the speed of SecOps.
Collection is no longer just log ingestion. In a composable SIEM, it becomes a security data fabric, the control point where data is shaped before it becomes expensive, rigid, or locked into a single system.
- Collect from any source: cloud, SaaS, network, endpoint, identity
- Normalize into common schemas or multiple schemas.
- Enrich with asset, identity, environment, and threat context.
- Shape, filter, and route data based on analytical intent.

Detection needs data, and it needs reliable, consistent data, but it does not require that all data be centralized, indexed, or treated equally. Modern security operations rely on multiple detection models, each optimized for a different purpose and time horizon:
- In-stream detection for real-time and near-real-time threats, where speed and precision are critical.
- Historical detection for low and slow, retroactive analysis, investigations, and hypothesis testing.
- Distributed detection across multiple environments, so analytics run where your data lives without forcing everything into a single pipeline.

.avif)
.webp)
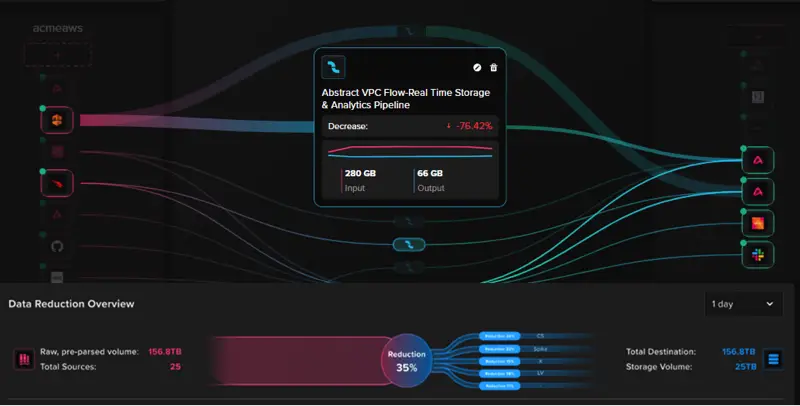
Not all security data has the same value, the same urgency, or the same lifecycle. A modern SIEM state of mind requires deliberately placing the right data into the right storage, in the right locations, for the right use cases.
Abstract enables that through three tiers:
- Real Time Storage for instantaneous retrieval, where milliseconds make the difference.
- Hot Storage for high-value, high-signal data that detection engines can access quickly.
- Warm Storage for cost-efficient retention that meets regulatory and compliance purposes.
.webp)
.webp)
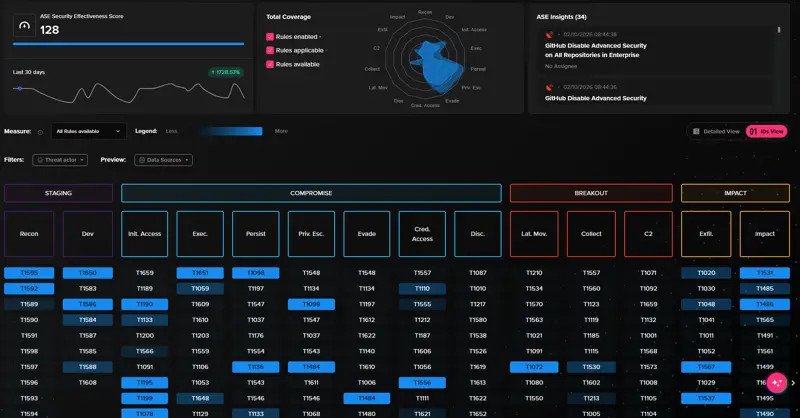
Security operations is where SIEM becomes real, and where AI must be deeply embedded, not bolted on. In a composable SIEM, SOC workflows operate as an AI-enabled control plane across the entire architecture, independent of where data lives or which engine produced the alert. This includes:
- AI-assisted triage and prioritization
- Context-rich investigations
- Proactive threat hunting
- A unified analyst workbench
- Response and SOAR workflows, all AI-enabled
.webp)

Start where your stack
NEEDS THE MOST HELP
Different teams start in different places. Abstract layers into your existing stack so you can improve what matters most without replacing everything.
ABSTRACTED
We’d love for you to be part of the journey. Let’s grab a coffee, have a chat, and set up a demo!
Your friends at Abstract — one of the most fun teams in cyber.
.avif)
Your submission has been received.