Where is Hotel California?
When I say SIEM is a state of mind, I mean it is less about a single product or vendor and more about an organizational philosophy. This is the difference between SIEM and Security Operations. The word operations assumes processes, customization, people (training, specialization, tasks) and business support. A state of mind is a mindset: an orientation toward how you design, deploy, and evolve security data systems. Just like Hotel California never meant a physical hotel, SIEM in the modern era isn’t confined to one appliance or monolith. It is the shared approach that guides how data is collected, normalized, stored, and leveraged for detection and response. In this sense, describing SIEM as a state of mind implies that it is not a destination but a perspective, a way of thinking that emphasizes adaptability, modularity, and choice.
"SIEM IS DEAD"
The current debate centers on federated/decoupled architectures vs. monolithic platforms vs AI-SOC. But if you step back, what SIEM has become is not a product, not even a platform in the old sense. SIEM is a state of mind. A metaphor for how organizations approach detection, response, and security data strategy. A system, yes, but a system of systems.
"NEXT-GEN SIEM IS NOT A SIEM"
Even before we founded Abstract, I used to say: “Next-Gen SIEM is not a SIEM.” At first it sounded provocative, even contradictory (they even made me take it off the website) but the vision was clear.
The phrase is multivalent.
"A new coat of paint"
The first interpretation is that what’s currently being marketed as “Next-Gen SIEM” doesn’t really qualify. Glorified logging and storage solutions with a new coat of paint. Most of the systems were designed to compete with Splunk back in 2012-15 and landed as acquisitions into larger security players.
Breaking the mold completely
The second interpretation is that the true next generation will not be a SIEM in the traditional, monolithic sense. It will break the mold completely.
Both are true. And both are already happening.
from monoliths to modular platforms
The future is modular and decoupled: a flexible, composable platform where each function can be swapped, scaled, or integrated. The value is not in the one-box solution, but in the architecture of choice. A system of systems.
.webp)
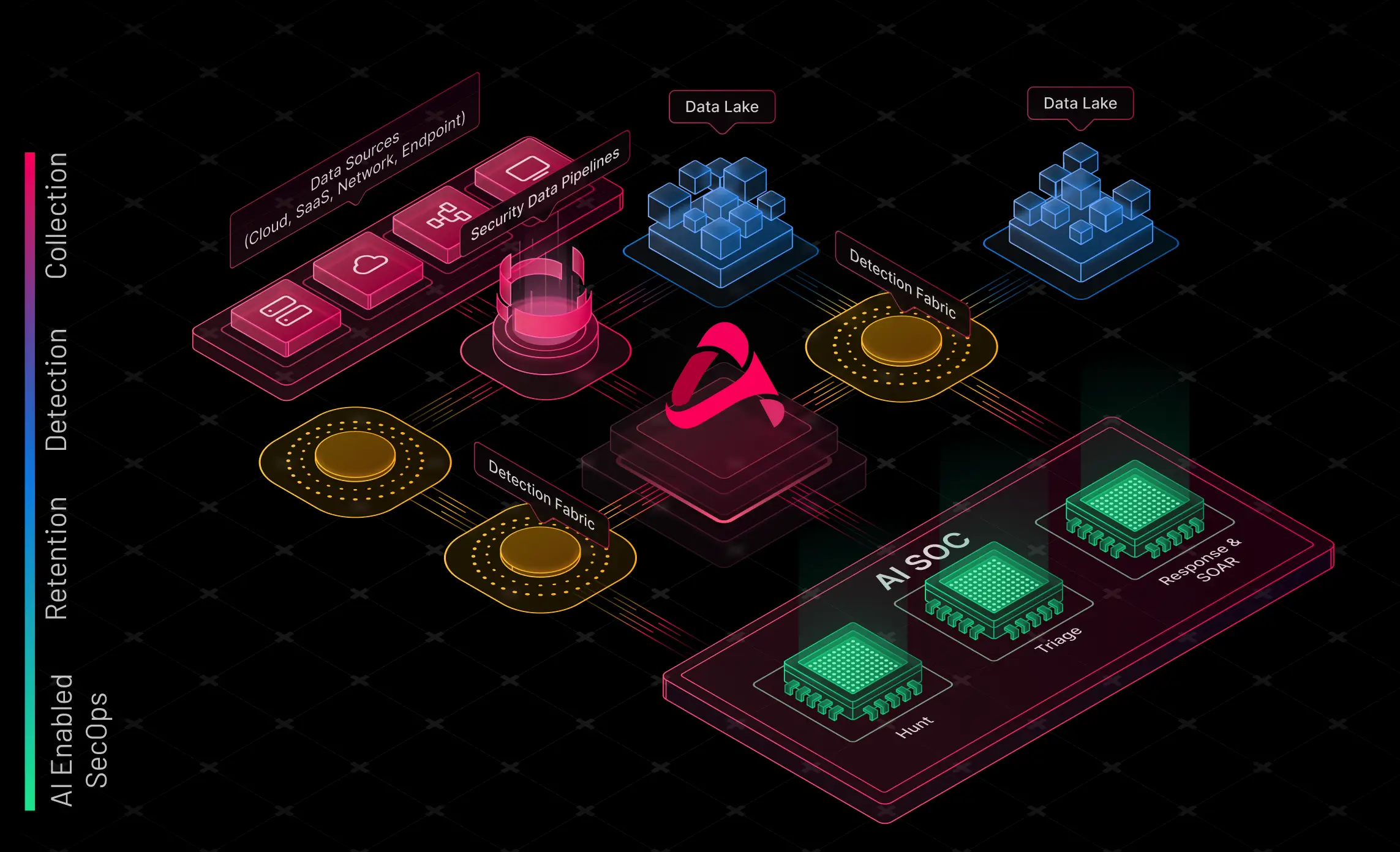
Key layers of a modern SIEM architecture include
Data strategy and collection

Flexible ingestion from any source
Pipelines

Shaping, enriching, and routing data efficiently
Data lake
.png)
Affordable long-term storage that meets regulatory and retention requirements
AI Enabled Workbench
.png)
A unified workbench for case management, hunting, response, and investigations leveraging the power of AI
AI Enabled Triage

Blending automated scoring with human-in-the-loop workflows
Automated response

Closed-loop playbooks, orchestration, and workflow integration
Oh, and AI right?
AI-SOC Is a Capability
AI-SOC is not a new category. It is not a replacement for SIEM. And It is not a destination architecture. AI-enabled security operations, the natural evolution of how humans interact with detection, investigation, and response workflows.
We’ve seen this movie before.
A decade ago, SOAR followed the exact same trajectory. It was launched as a standalone category, positioned as something adjacent to SIEM. New companies emerged, new acronyms were invented, and new buying motions followed. Then reality set in. As soon as SOAR became operationally relevant, SIEM vendors we re forced to absorb it. Every major SIEM either acquired a SOAR company or rebuilt the capability in-house. The separation was artificial and temporary.
AI-SOC will follow the same path.
Standalone AI-SOC vendors will feel pressure to build more and more SIEM-like functionality: data access, normalization, context, storage, correlation, and detection logic. At the same time, SIEM platforms will continue to embed AI deeper into investigations, triage, response, and analyst workflows. Over time, the distinction collapses not because of marketing, but because security operations demand it.
AI does not replace SIEM. It augments it.
Without access to normalized, high-fidelity security data, AI is blind. Without historical context, AI is shallow. Without streaming data, AI is late. And without workflow integration, AI is academic.
AI-SOC only works when it is deeply embedded into the security data lifecycle:
During ingestion and enrichment
During detection and scoring
During triage and investigation
During response and learning loops
Composable SIEMfor the AI GenerationAI-GEN
Deconstructing SIEM Into Its
Fundamental Building Blocks
Collection: The Security Data FAbric
Collection is no longer just log ingestion. In a composable SIEM, it becomes a security data fabric, the control point where data is shaped before it becomes expensive, rigid, or locked into a single system.
This layer includes:
- Collecting from any source: cloud, SaaS, network, endpoint, identity
- Normalization into common schemas (or multiple schemas)
- Enrichment with asset, identity, environment, and threat context
- Data shaping, filtering, and routing based on intent
This is where organizations regain control over data gravity and cost. Not all data needs to be indexed. Not all data needs to be retained forever. And not all data needs to land in the same platform.
Composable SIEM allows this layer to stand on its own, feeding multiple downstream systems rather than serving a single monolithic SIEM. This is the data control plane.
Detection Fabric: Signal at Speed
Detection is about immediacy, the ability to identify threats while they are still unfolding, when response still matters and context has not yet gone cold. In modern environments, detection is no longer a single engine running against a single dataset. It is a set of capabilities that must operate across time, scale, and data location.
Detection needs data, and it needs reliable, consistent data, but it does not require that all data be centralized, indexed, or treated equally. Modern security operations rely on multiple detection models, each optimized for a different purpose and time horizon:
- In-stream detection for real-time and near-real-time threats, where speed and precision are critical
- Historical detection for low and slow, retroactive analysis, investigations, and hypothesis testing
- Federated detection and search that executes analytics where data already lives, without forcing wholesale ingestion
In a composable SIEM, detection logic is portable. It can be pushed into the data stream, executed against historical stores, or federated across external systems. This allows organizations to detect threats at the right moment, using the right data, without paying unnecessary cost or introducing architectural rigidity. The shift is subtle but important: detection is no longer bound to storage. It is a capability that can be composed, scaled, and evolved independently. This is what enables organizations to prioritize signal over noise, speed over bulk, and outcomes over ingestion volume.
Retention: Context at Scale
Most organizations are paying a tremendous tariff on security data storage. The reality is that the majority of security data that gets collected is never used for detection, investigation, or response. Instead, it accumulates in what has effectively become a data swamp, expensive to maintain, difficult to manage, and rarely delivering proportional value.
This is not a tooling failure. It is a data strategy failure.
Not all security data has the same value, the same urgency, or the same lifecycle. A modern SIEM state of mind requires deliberately placing the right data into the right storage, in the right locations, for the right use cases.
Key considerations include:
- Data residency requirements, which may dictate where certain data must physically live
- Transfer and egress costs, particularly in multi-cloud and hybrid environments
- Latency and access needs, depending on whether data supports real-time detection, investigations, or long-term analysis
- Use case alignment, distinguishing between data required for active threat detection and data retained primarily for regulatory, audit, or compliance purposes
Some data is critical for real-time and near-real-time detection. Other data is rarely, if ever, queried, but must be retained for regulatory, legal, or forensic reasons. Treating all data the same, ingesting it, indexing it, and storing it in a single system is what drives runaway costs and architectural rigidity.
Composable SIEM enables tiered and federated retention strategies, allowing organizations to keep high-value, high-signal data close to detection engines while placing lower-value or regulatory data into cost-efficient storage that still remains accessible when needed.
The goal is not to just store less data. The goal is to store data intelligently.
By aligning retention strategy with actual security and business outcomes, organizations can escape the data swamp, reduce cost, and preserve the context that matters without forcing everything into a single analytics or storage platform.
AI-Enabled Security Operations (AI-SecOps)
Security operations is where SIEM becomes real, and where AI must be deeply embedded, not bolted on. In a composable SIEM world, SOC workflows operate with AI as an enabler across the entire architecture, independent of where data lives or which engine produced the alert.
This includes:
- AI-assisted triage and prioritization
- Context-rich investigations
- Proactive threat hunting
- A unified analyst workbench
- Response and SOAR workflows, all AI-enabled
At its core, AI-SecOps is about enabling analysts, not replacing them.
AI-SecOps is a core building block, designed to amplify how analysts triage alerts, investigate incidents, hunt threats, and execute response. Its power does not come from models alone, but from deep integration with the data fabric, detection logic, and operational context that already exist within the SIEM.
When AI is embedded directly into these workflows, it reduces cognitive load, accelerates decision-making, and allows analysts to spend more time on judgment and less time on mechanics. AI helps connect signals across detections, summarize context across datasets, and surface the why behind alerts, not just the what.
This only works when the architecture supports it. Composability without AI becomes inefficient, forcing analysts to manually stitch together data, detections, and tools at human speed. Together, AI and composability enable something different: security operations that scale with data, adapt with threats, and remain grounded in how analysts actually work. That is what defines modern security operations.
THe Future of SIEM ARCHITECTURE










.png)