Gainsight Breach: SaaS Supply Chain Attack Exposes Salesforce Integrations
Background
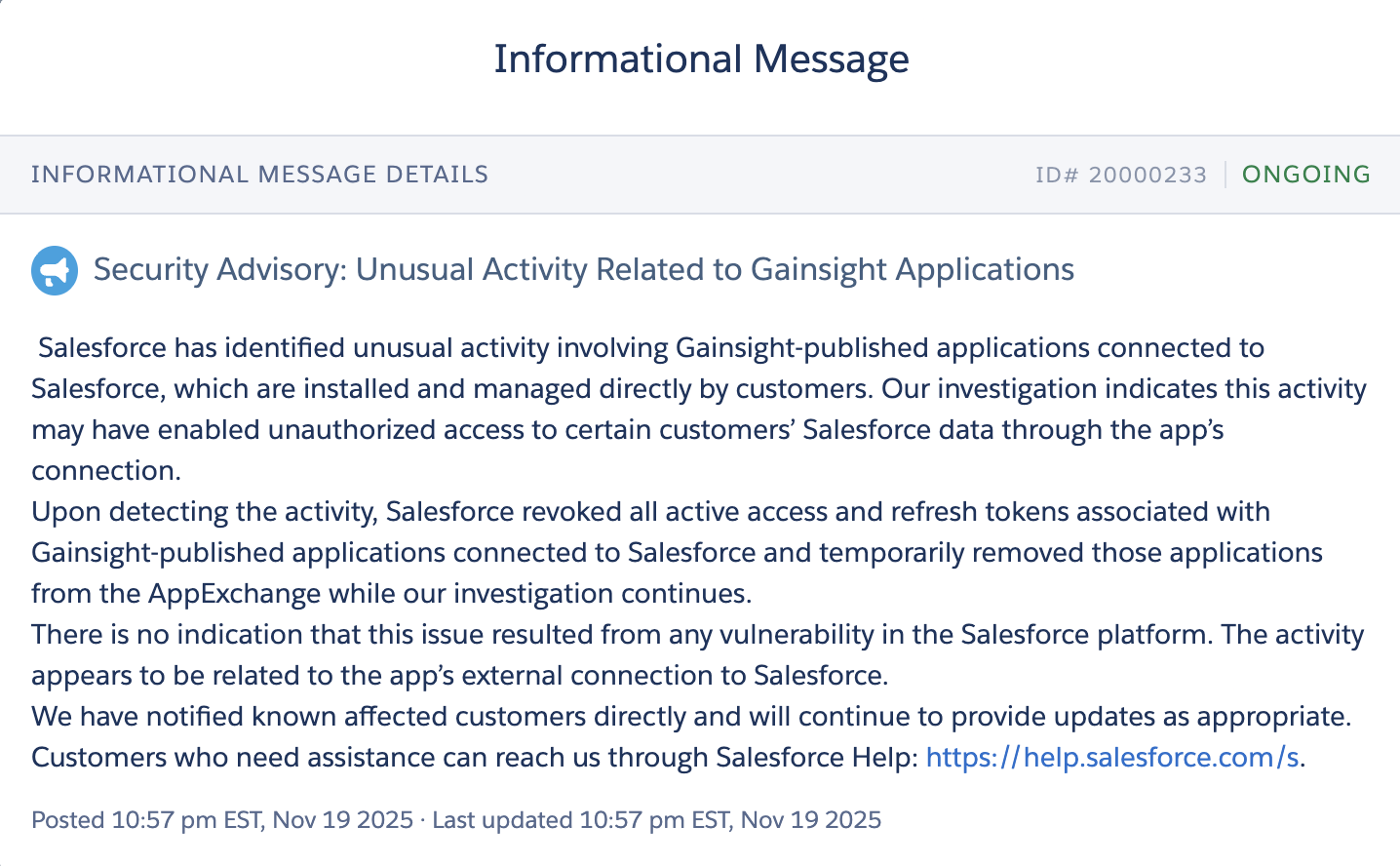
On November 19, 2025, at 10:57 PM EST, Salesforce issued a security advisory (ID# 20000233) disclosing unusual activity involving Gainsight-published applications. The advisory stated that their investigation indicated "this activity may have enabled unauthorized access to certain customers' Salesforce data through the app's connection."
This attack follows a familiar pattern. ShinyHunters gained initial access to Gainsight during the Salesloft Drift hack earlier in 2025, maintaining access for nearly three months. The threat actors discovered that data stolen from Salesloft Drift enabled entry points into numerous systems, creating a cascading supply chain compromise that continues to impact organizations months after the initial breach.
The scope of the compromise continues to expand. Scattered Spider (also known as Scattered Lapsus$ Hunters, which includes ShinyHunters) has announced plans to publish a new data dump site on November 24th containing Salesforce information from over 300 companies. This announcement underscores both the scale of the breach and the threat actors' intent to continue leveraging stolen data for extortion and public exposure.
The attack exploits the trust relationship between platforms and third-party integrations, leveraging compromised OAuth tokens and digital keys that allow apps to access data without sharing user credentials. Rather than attacking Salesforce directly, threat actors compromise the connective tissue between services the OAuth tokens and API integrations that organizations rely on for business operations.
The Attack Chain
The mechanics of this attack mirror the August 2025 Salesloft Drift campaign. Attackers used stolen OAuth tokens for third-party integrations with Salesforce to steal sensitive information including passwords, AWS access keys, and Snowflake tokens from customers' Salesforce instances. Because these OAuth tokens provide legitimate API access, the malicious activity can blend with normal application behavior, making detection challenging without proper monitoring.
Upon detecting the activity, Salesforce revoked all active access and refresh tokens associated with Gainsight-published applications and temporarily removed those applications from the AppExchange. However, according to ShinyHunters, Salesforce detected the unauthorized activity about a week or two after the initial intrusion a delay that allowed significant data exfiltration.
Abstract Detection Coverage
We've developed comprehensive detection rules specifically designed to identify these attack patterns within Salesforce environments. Our detection portfolio addresses each stage of the attack chain:
Administrative Security
- Salesforce_-_Admin_Impersonation_Detected - Identifies attempts to impersonate administrator accounts
- Salesforce_-_Credential_Stuffing_Attack - Detects credential stuffing campaigns targeting Salesforce instances
Authentication Monitoring
- Salesforce_-_Multiple_Failed_Login_Attempts - Flags brute force and password spraying activities
- Salesforce_-_Successful_Login_After_Failed_Attempts - Identifies successful compromise after failed authentication attempts
- Salesforce_-_Suspicious_Session_Activity - Detects anomalous session patterns that may indicate token abuse
Data Exfiltration Detection
- Salesforce_-_Bulk_API_Data_Extraction - Identifies large-scale data retrieval through API calls
- Salesforce_-_Large_API_Data_Response - Monitors for unusually large API responses indicating bulk data access
- Salesforce_-_Large_Report_Export_Detected - Detects mass export of reports that could contain sensitive data
- Salesforce_-_Multiple_Report_Exports - Identifies patterns of report generation and export consistent with data theft
API Abuse and Query Monitoring
- Salesforce_-_REST_API_Query_Abuse - Detects anomalous REST API query patterns
- Salesforce_-_Unusual_Apex_Execution - Identifies suspicious execution of Apex code that could indicate backdoor access
These detection rules operate on the telemetry sources available within Salesforce Login History, Setup Audit Trail, and Event Monitoring data providing visibility into the exact attack techniques used in the Gainsight and Salesloft campaigns. By monitoring for these patterns in real-time, organizations can identify compromise during the attack rather than learning about it weeks later through vendor notifications.
Recommendations
Organizations using Salesforce with third-party integrations should take immediate action:
- Audit Connected Applications: Review all OAuth-connected applications in your Salesforce instance. Remove or restrict any integration that doesn't require broad API access.
- Rotate OAuth Tokens: Treat any OAuth token with broad permissions as high-risk and rotate credentials immediately for all third-party integrations.
- Implement Real-Time Monitoring: Deploy detection rules that can identify anomalous data access, bulk exports, and authentication anomalies as they occur.
- Review API Permissions: Apply the principle of least privilege to all connected applications, ensuring they can only access the specific objects and fields required for their function.
- Enable Comprehensive Logging: Ensure Event Monitoring is enabled and that logs are being collected, normalized, and analyzed in real-time not just retained within Salesforce's 30-day window.
Conclusion
The Gainsight breach demonstrates that SaaS supply chain attacks will continue to be a primary vector for data theft. ShinyHunters explicitly stated that Gainsight was "just a test to probe how much monitoring there is now", suggesting additional attacks targeting other OAuth integrations are likely. With Scattered Spider's announcement of a November 24th data dump containing information from 300+ companies, the full scope of this campaign is only beginning to emerge.
Organizations can no longer rely on their SaaS providers to detect and prevent these attacks on their behalf. It is imperative to view this as a signal to audit SaaS environments, including conducting regular reviews of all third-party applications connected to Salesforce instances. More importantly, security teams need the telemetry and detection capabilities to identify these attacks as they unfold.
With proper monitoring in place covering authentication, authorization, data access, and API usage patterns these attacks become detectable. The question is whether organizations will wait for the next vendor notification or take control of their SaaS security posture now.
ABSTRACTED
We would love you to be a part of the journey, lets grab a coffee, have a chat, and set up a demo!
Your friends at Abstract AKA one of the most fun teams in cyber ;)
.png)
Your submission has been received.