Automating macOS Incident Response: DFIR-as-Code in Action Against AppleProcessHub
AppleProcessHub and the Application of DFIR-as-Code in MacOS Incident Response
Digital forensics has historically relied on manual collection, inspection, and interpretation—an approach ill-suited for modern operational demands. With increasingly distributed environments and rapid adversary movement, a more scalable, consistent methodology is needed. DFIR-as-Code proposes such a methodology. By encoding forensic and response workflows into reusable logic, organizations can transition from reactive, one-off analyses to systematic, verifiable, and expedited incident response.
We introduced the concept of DFIR-as-Code in our previous post, of this series (https://www.abstract.security/blog/dfir-as-code-scaled-and-repeatable-incident-response). This approach helps programmatically deliver repeatable forensic and response actions collecting consistent data across incidents, analysts and teams.
A recent case involving the AppleProcessHub malware provides a practical context in which to examine the application of DFIR-as-Code within a MacOS environment. This malware specimen, catalogued in public repositories and identified as both an infostealer and a trojan, offers a compelling use case for standardized forensic automation.
AppleProcessHub Overview
AppleProcessHub is a malicious Mach-O binary that, upon execution, deploys a Bash script. A deep dive of this malware is available from Kandji here(https://www.kandji.io/blog/macos-appleprocesshub-stealer ) This script exfiltrates a set of commonly targeted configuration and credential files, including:
- Shell history (.bash_history, .zsh_history)
- Git configuration in .gitconfig
- SSH configurations and key files
- MacOS keychain databases in Login.keychain-db
The nature of these targets underscores a central concern in most modern intrusions: credential theft. Once exfiltrated, these credentials enable lateral movement, privilege escalation, or external access from attacker-controlled infrastructure. For organizations reliant on manual triage, identifying such theft is a race against time—with inconsistent results. By contrast, DFIR-as-Code enables immediate detection, categorization, and escalation of these indicators.
Instrumenting the Response: Codified Triage of AppleProcessHub Artifacts
Using DFIR-as-Code principles, a security team can define specific countermeasures that automatically process secondary data sources such as filesystem images and memory captures. In the case of AppleProcessHub, the following countermeasures are relevant:
1. Credential Artifact Detection with Yara
Yara is a powerful rules language which is used to describe file contents and attributes. Frequently used to describe malware and their corresponding families, Yara can also be leveraged to detect credential files. Below is an example of a Yara rule to detect SSH private keys:
You can use this methodology to describe dozens of different types of credential files. If you find these important files on a compromised system, you should immediately audit and revoke them to prevent further credential abuse. A few examples of credentials worth alerting on include:
These yara rules in our public GitHub repository here.
Once codified, this logic can be systematically applied to forensic captures, ensuring that credential exposure is identified early in the investigative process. Countermeasures can then be tied to response actions such as initiating credential rotation or notifying appropriate identity governance systems.
In this example, the Abstract Security Platform enables alerting on SSH private keys found on the imaged system. This allows the system to immediately identify and escalate the discovery of credentials on a compromised asset.
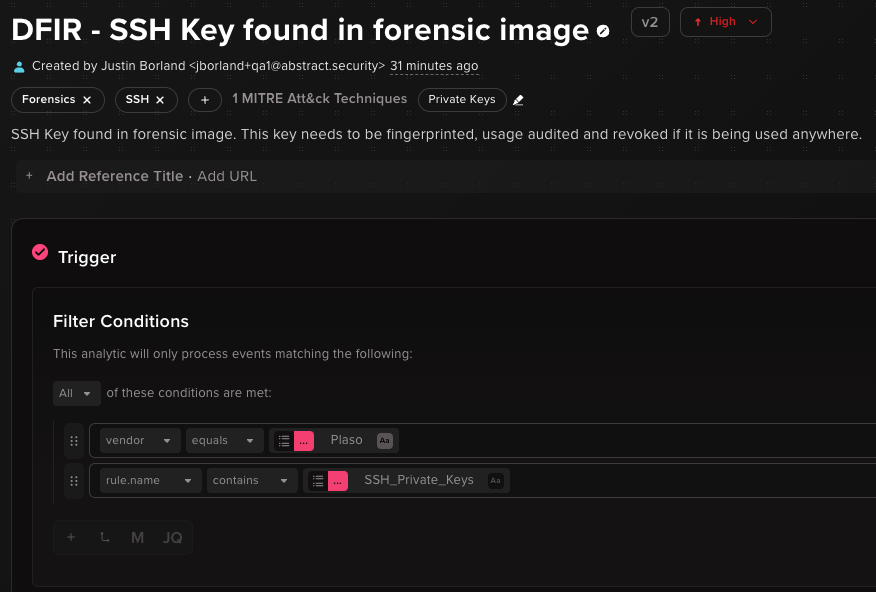
Instrumenting basic alerting criteria around your secondary data sources and curated countermeasures enables foundational blocks upon which to expand and build.
Once deployed, immediate notification and escalation of the affected keys can be generated and actioned, as seen in our Abstract Security findings. This can be expanded to target any credentials which may be present in your environment.
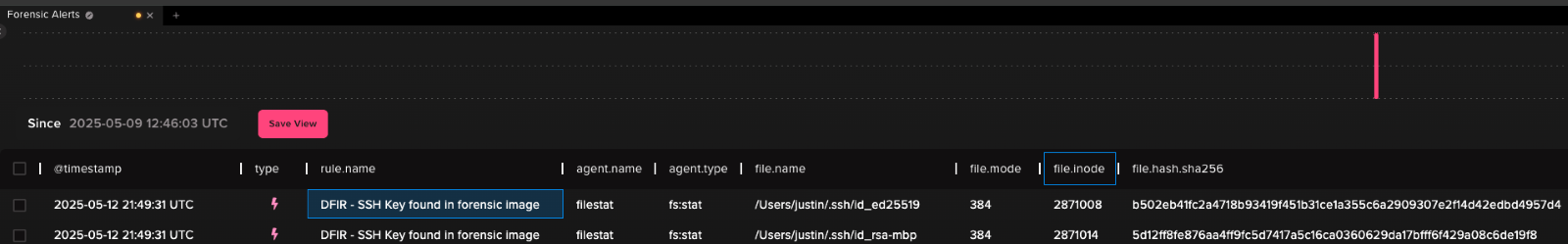
Immediate detection and triage of potentially compromised credentials will help DFIR teams “shift left” and reduce mean-time-to-remediation, potentially saving them from additional abuse or exploitation.
2. Processing with Plaso
Plaso or similar tools enable automated extraction and categorization of MacOS keychain contents. Within a DFIR-as-Code pipeline, these parsers operate on every imaged MacOS endpoint, extracting credentials tagged as either macos:keychain:application or macos:keychain:internet.
Below is an example of a Nextcloud macos:keychain:application entry:
The goal is twofold: to identify what services may have been accessed with these credentials, and to quantify the risk surface that must be mitigated. Keychain records—containing application or web credentials—are often neglected in manual reviews but are particularly valuable to attackers. Automating their collection and review ensures that no sensitive data type is overlooked.
During an incident, your team must quickly determine what the compromised system had access to. This enables timely triage, containment, and remediation. DFIR-as-Code aims to minimize wasted time and maximize the speed and depth of analysis.
Below is an example rule that detects MacOS keychain entries not built into the system.

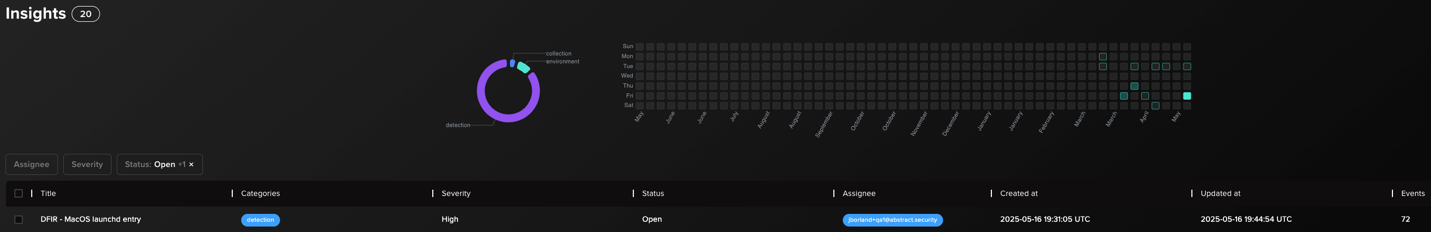
This rule allows us to quickly triage credentials that may have been exposed during an incident and immediately begin containment and remediation. Below is an example of insights and findings generated by rapidly identifying the keychain scope of impact.


3. Persistence Mechanism Identification
In the MacOS ecosystem, the launchd subsystem is frequently co-opted by malware for persistence. While default services and agents are well-documented, malware often creates additional .plist files within user or system launch directories such as:
By deploying comparison rules against known baselines, security teams can isolate non-standard entries that may indicate malicious behavior. These entries can be automatically triaged and flagged for further analysis, reducing the time analysts spend identifying persistence mechanisms in compromised environments.
Below is an example rule that detects non-default launchd entries found on the imaged system:

This DFIR-as-Code countermeasure is ideal for quickly triaging MacOS persistence mechanisms utilizing launchd. Some examples of benign entries, like Zoom, VirtualBox, and GoogleUpdater can be seen in the figure below.
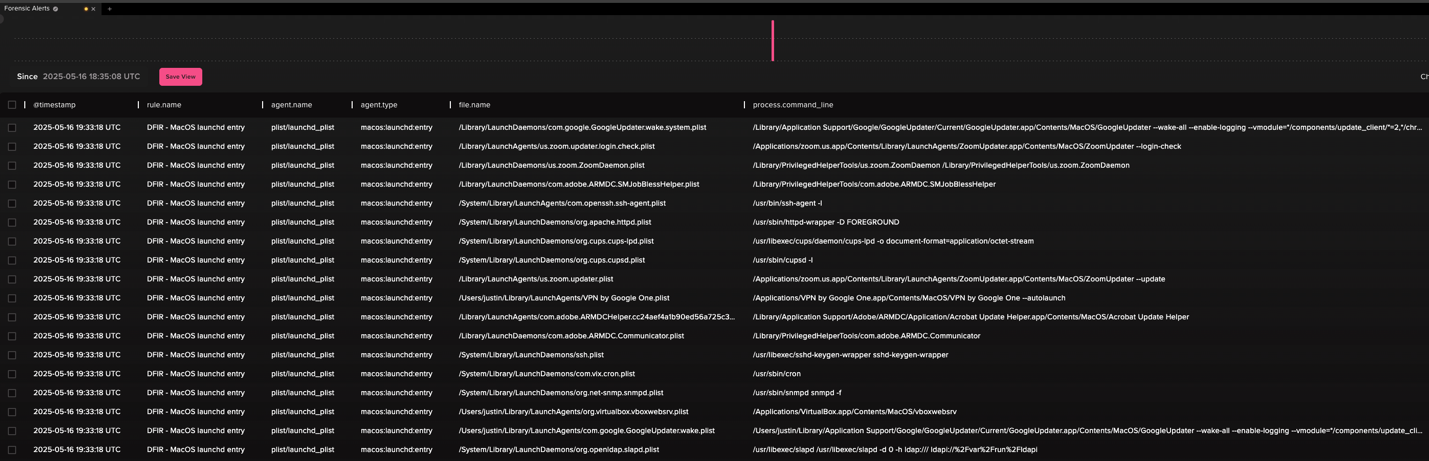
As with other valuable forensic findings, your team can generate insights that help engineers and analysts track and understand the full scope of the incident. You can quickly route tickets to the appropriate teams for immediate remediation. This approach reinforces the “shift left” methodology by delivering relevant information to analysts promptly, allowing them to make faster, more informed decisions with reduced risk.
Structured Application: When, Who, What, and How
To standardize the response to AppleProcessHub and other mac malware intrusions, DFIR-as-Code breaks the incident response process to focus on the following questions:
- When: Timestamp correlation and alert ingestion establish the timeline of the incident.
- Who/What: The user identities and compute resources that have been impacted. This can include hostnames, usernames, API keys, non-human identities, IP addresses and more. Identifying the Who and What allows for secondary data acquisition via automation and human analysis to understand the scope of intrusion.
- How: The operations that occurred in the intrusion.
Using DFIR-as-Code allows teams to detail each of these areas in a version-controlled and auditable manner, ensuring that forensic techniques are uniformly applied across incidents and time.
Reducing Variability and Human Error
A central concern in incident response is inconsistency between analysts. Two individuals reviewing the same forensic image are unlikely to produce identical findings unless provided with a standardized playbook. DFIR-as-Code mitigates this discrepancy by removing procedural ambiguity. Every analyst inherits the same operational tooling, the same decision logic, and the same forensic lens.
This methodology transforms DFIR into a science—not in abstraction, but in execution. For AppleProcessHub, and for future incidents involving similar tactics, this approach ensures that investigative depth is achieved without sacrificing speed or reproducibility.
Continuous Expansion Through Libraries of Countermeasures
The strength of DFIR-as-Code lies not only in its reproducibility but in its extensibility. Organizations may build libraries of countermeasures tailored to specific platforms or malware families. Over time, these collections evolve into institutional memory—codified, scalable, and easily audited.
For AppleProcessHub and similar MacOS threats, relevant countermeasure categories include:
- Credential detection via YARA and parsing logic
- Launchd anomaly detection
- Keychain analysis and service attribution
- Exfiltration pattern recognition in memory and disk artifacts
Generally this can take many forms:
- SIEM and Sigma rules for secondary data sources (Plaso output)
- Advanced analytics using deterministic logic or probabilistic machine learning and AI tooling
- Yara rules for file and memory images
- Python scripts for advanced use cases and Response procedures to quickly implement required actions
- Data models and correlation rules
And more
Below are some examples of DFIR-as-Code countermeasures and response procedures which can be automated to speed up investigations, freeing engineering resources:
Each countermeasure is independently testable, allowing organizations to progress through a well-defined lifecycle: from initial detection, to controlled blocking, and finally to estate-wide deployment.
Conclusion
The emergence of malware like AppleProcessHub highlights is an example of a threat targeting MacOS systems. DFIR-as-Code provides the necessary framework to bring parity between platform complexity and response capacity.
DFIR-as-Code gives your organization’s Security Operations team a powerful force multiplier. When handling complex incident response scenarios, your team can quickly evaluate the exposure of an incident to effectively respond. The result is reduced containment time and accelerated eradication efforts. This framework enables rapid development of use cases which enables further automation.
When your team understands what data an attacker exfiltrated during an incident, they can significantly reduce the time needed for incident disclosure. In some environments, teams must send out notifications within hours, not days or weeks. Automating these elements of the incident response process enables SecOps teams to respond faster and more effectively. Continuously evolving your detection and prevention controls helps close exploitable gaps, while DFIR teams keep expanding their libraries of detection and response capabilities.
By embracing DFIR-as-Code, your team actively detects and signals threats from slower, more complex data sources. With forensic images and memory dumps, you don’t just improve response times; you transform digital forensics from a reactive process into a proactive, adaptive capability. As your organization matures these practices, you build intelligent incident response pipelines that scale with complexity, reduce human error, and stay ahead of modern threats.
ABSTRACTED
We would love you to be a part of the journey, lets grab a coffee, have a chat, and set up a demo!
Your friends at Abstract AKA one of the most fun teams in cyber ;)
.avif)
Your submission has been received.